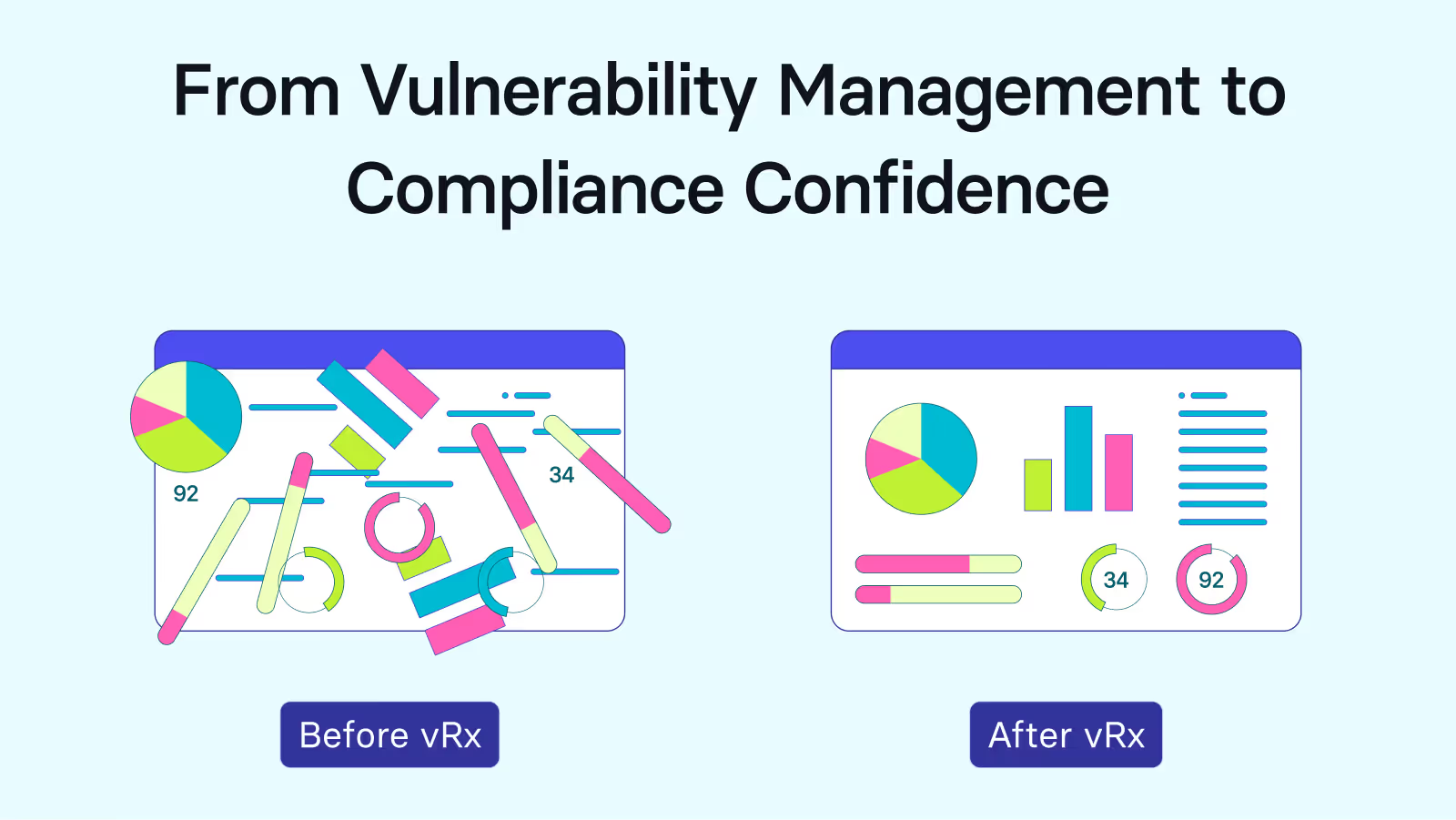
Vulnerability management is no longer just a technical function; it's a core component of enterprise compliance. Yet, most organizations still struggle to align their vulnerability management practices with the frameworks that govern their compliance audits NIST CSF, ISO 27001, CIS Controls, and others.
Enter the Vicarius vRx Maturity Model: a groundbreaking framework that doesn’t just assess your security maturity but actively translates it into measurable progress against globally recognized compliance standards. This model is not theoretical. It’s operational. It’s practical. And most importantly it’s built to evolve your business from reactive patching to fully automated compliance-driven security.
Why Vulnerability Management Is Core to Compliance
Regulatory standards such as NIST CSF 2.0, CIS Controls v8, and ISO/IEC 27001:2022 don’t just recommend vulnerability scanning; they mandate it. Whether you’re aiming for SOC 2 compliance, preparing for a HIPAA audit, or aligning with ISO 27001 controls, continuous vulnerability management is foundational.
Yet here’s the problem: most compliance programs fail to connect operational vulnerability actions (like patching or detection) to formal compliance language. That’s where Vicarius changes the game.
The vRx Maturity Model: Bridging Compliance and Execution
The vRx Maturity Model organizes your vulnerability management operations into five progressive stages:
- Deploy – Establish visibility and coverage across your assets.
- Detect – Continuously discover vulnerabilities across all endpoints.
- Analyze – Prioritize threats based on contextual risk and exploitability.
- Remediate – Apply patches, scripts, or virtual patching automatically.
- Automate – Orchestrate end-to-end workflows with self-healing systems.
Each stage maps directly to controls from NIST CSF 2.0, CIS Controls v8, and ISO/IEC 27001, making it a universal compliance translation layer. For example:
- Deploy maps to NIST “Identify” and ISO 27001 A.5.7 (Asset Inventory)
- Detect aligns with CIS Safeguard 7 and ISO 27001 A.8.8 (Vulnerability Management)
- Remediate supports CIS IG3 Patch Applications and ISO 27001 A.12.6.1
This mapping allows organizations to track, report, and improve their compliance posture without duplicating effort across tools.
Achieving Compliance Automation with vRx
Traditional compliance is a painful process of manual evidence collection, audit prep, cross-team alignment, and reactive fixes. With Vicarius, that entire workflow is orchestrated.
Here’s how:
- Automated Deployment – Agents are rolled out across your environment, maintaining real-time asset visibility.
- Continuous Detection – vRx integrates with multiple threat intelligence feeds, automatically identifying emerging vulnerabilities.
- Risk-Based Analysis – Using AI-driven risk scoring, vulnerabilities are prioritized by exploitability and asset criticality.
- Scripted & Patchless Remediation – Even zero-day or unpatchable issues are mitigated through pre-built scripts or virtual patching.
- Compliance Dashboarding – Every remediation action is tracked, validated, and aligned to industry benchmarks.
No more siloed scans. No more spreadsheet chaos. Just a unified platform that aligns operational activity with strategic compliance goals.
How Mature Is Your Security Operation?
Vicarius enables organizations to self-assess using a straightforward questionnaire across the five stages. Each stage is scored from 1 (manual, reactive) to 5 (automated, optimized). The score reveals your current maturity level:
- Operational (5–7) – Minimal coverage, mostly manual effort.
- Emerging (8–12) – Some automation, but gaps remain.
- Foundational (13–17) – Processes established, risk-driven prioritization in place.
- Advanced (18–22) – Proactive posture with integrated tools and automated patching.
- Optimized (23–25) – Self-healing systems, real-time compliance alignment, near-zero manual intervention.
Use this to improve security and to demonstrate continuous compliance progress to your board, auditors, or CISO.
Real Value for Real Roles in Vulnerability Management and Compliance
Cybersecurity today demands more than reactive tools and siloed teams. It requires unified visibility, coordinated response, and compliance that is built into every step of the security workflow. Vicarius vRx delivers all of this by aligning operational security activity with globally recognized frameworks like NIST CSF 2.0, CIS Controls v8, and ISO/IEC 27001 while meeting the specific needs of every role in your organization.
Chief Information Security Officers (CISOs) gain a real-time, organization-wide map of compliance progress across all sites and departments. The Vicarius vRx Maturity Model offers strategic oversight that translates technical operations into measurable outcomes. This enables better board reporting, more accurate risk assessments, and the ability to track continuous improvement in alignment with global standards.
Compliance Officers benefit from pre-mapped evidence that directly aligns remediation activities to audit requirements. Rather than compiling documentation manually, vRx connects every security control deployment, detection, remediation to recognized compliance clauses. This provides clarity, reduces audit preparation time, and improves confidence during reviews and certifications.
Security Engineers are empowered with automation that goes beyond visibility. Instead of managing endless vulnerability scan reports, they use vRx to perform real remediation through automated patching, script-based fixes, and virtual patching. Prioritization is driven by risk, not guesswork enabling faster resolution of critical issues with fewer manual steps.
IT Operations teams see tangible efficiency gains by orchestrating remediation through their existing ecosystem of tools whether it’s ITSM platforms like ServiceNow or SysAid, endpoint detection tools like CrowdStrike or Cortex, or orchestration systems like SOAR and RMM. Vicarius vRx becomes the connective layer that unifies tools, teams, and actions across the enterprise.
Start Where You Are. Automate Where You Can. Advance Where It Counts.
Compliance doesn’t begin with an audit. It begins with visibility. It grows through consistency. It succeeds with automation.
The Vicarius vRx Maturity Model is your guide to scaling these efforts while reducing overhead, aligning with global standards, and strengthening your cyber resilience.
Whether you’re a CISO guiding strategy, a compliance lead preparing audits, a security engineer remediating threats, or an IT operator running infrastructure, Vicarius vRx is designed to work with you not just for you. It’s not just about finding vulnerabilities it’s about fixing them, proving it, and moving forward with confidence.
Book a live demo to see automated compliance in action