
LockBit is not just another ransomware group. It is arguably the most aggressive and technically advanced threat actor operating in the Ransomware-as-a-Service (RaaS) ecosystem today. Since 2019, LockBit’s affiliates have targeted organizations across the globe, evolving from a single strain to a modular attack platform capable of crippling hybrid IT environments in hours. From Windows and Linux to VMware ESXi and backup systems, no surface is safe.
This blog breaks down LockBit’s evolution, the full attack lifecycle, and how defenders from CISOs to IT administrators can operationalize mitigation using tools like Vicarius vRx.
The Evolution of LockBit: From Commodity to Complex
LockBit began as a typical RaaS operation in 2019, but by 2021, it had outpaced many peers. LockBit 2.0 introduced faster encryption and better evasion; LockBit 3.0 (aka LockBit Black) in 2022 borrowed techniques from BlackMatter and BlackCat, making it harder to detect and more adaptable across platforms.
By 2025, LockBit supported encryption of:
- Windows, including Server 2012–2022
- Linux, including file servers and Docker containers
- VMware ESXi, allowing attackers to ransom dozens of VMs simultaneously
- macOS (partially), via beta payloads
LockBit’s payloads are now password-protected, modular, and often customized per target. They check system language to avoid CIS countries, escalate privileges, disable security tools, and even delete backups before detonation.
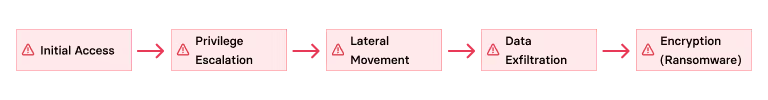
LockBit’s Attack Lifecycle: Kill Chain Breakdown
LockBit affiliates follow a relatively consistent kill chain. Let’s unpack the key stages.
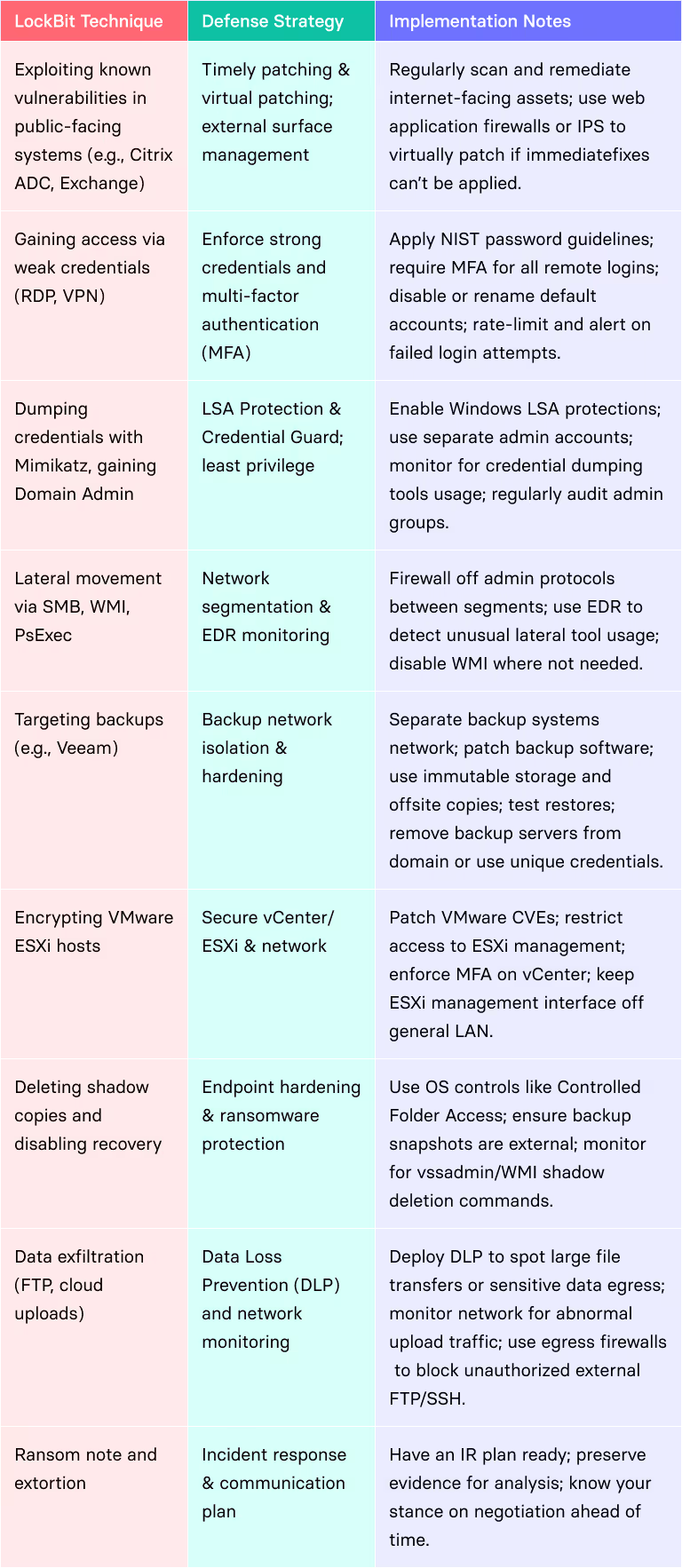
1. Initial Access
LockBit attackers leverage:
Known vulnerabilities, especially in exposed services like PaperCut (CVE-2023-27350), Citrix ADC (CVE-2023-4966), and Exchange ProxyShell (CVE-2021-34473)
- Weak RDP or VPN credentials, often guessed or purchased
- Phishing, to drop Cobalt Strike or initial implants

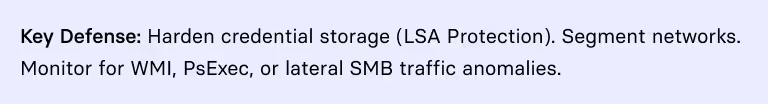
2. Privilege Escalation & Lateral Movement
Once inside, affiliates deploy Cobalt Strike or custom RATs, then:
- Dump credentials using Mimikatz
- Elevate privileges via Zerologon (CVE-2020-1472) or hash reuse
- Move laterally with SMB, WMI, PsExec
They often disable EDR, remove legitimate admins from domain controllers, and establish persistence via new admin accounts.
3. Targeting Crown Jewels: Backups, ESXi, NAS
LockBit prioritizes:
- Veeam backup servers (via CVE-2023-27532)
- VMware ESXi hosts (via exploits like CVE-2021-21972)
- NAS/file servers with open SMB shares or default credentials
Before encryption, affiliates often delete or exfiltrate backups and shut down VMs, ensuring maximum disruption.

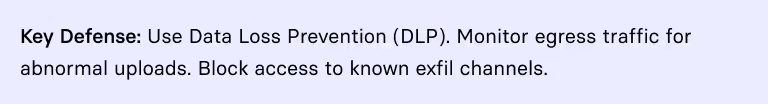
4. Data Exfiltration and Double Extortion
Before launching encryption, LockBit steals sensitive data (HR records, IP, financials) using tools like Rclone, FileZilla, or cloud uploads. They then threaten to leak data on their Tor-based leak site if ransom demands aren’t met.
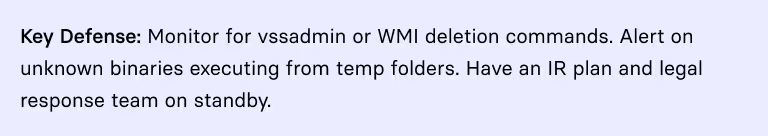
5. Ransomware Deployment
LockBit uses:
GPOs or PsExec to mass-deploy payloads
- Command-line flags for Safe Mode encryption
- WMI to delete Volume Shadow Copies
- Multithreaded AES encryption, targeting documents, databases, and VMs
Ransom notes appear with a Tor link for negotiations. Demands range from $10,000 to over $1 million with discounts for Monero payments to hide the money trail.
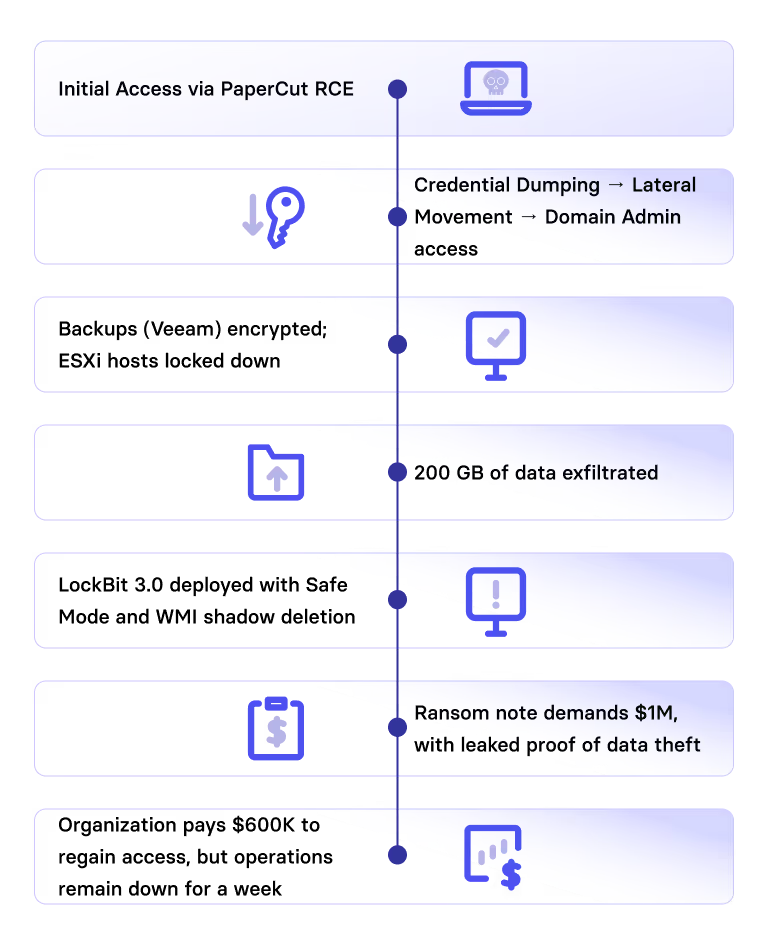
2025 Case Study: A LockBit Breach in Action
A mid-sized enterprise running an outdated PaperCut server (CVE-2023-27350) was breached in early 2025:
- Initial Access via PaperCut RCE
- Credential Dumping → Lateral Movement → Domain Admin access
- Backups (Veeam) encrypted; ESXi hosts locked down
- 200 GB of data exfiltrated
- LockBit 3.0 deployed with Safe Mode and WMI shadow deletion
- Ransom note demands $1M, with leaked proof of data theft
- Organization pays $600K to regain access, but operations remain down for a week
Strategic Defense for CISOs
CISOs must own the LockBit risk at the enterprise level. Focus on:

Tactical Defense for Security and IT Teams
How Vicarius vRx Stops LockBit in Its Tracks
Vicarius delivers automated, real-time defense against LockBit’s tactics. Here’s how:

Final Thoughts
LockBit has evolved into a professional extortion business. It exploits gaps in patching, credential hygiene, and segmentation. Its affiliates are opportunistic, fast-moving, and well-resourced.
But this is a solvable problem.
With disciplined patching, hardened configuration, and the right tools like Vicarius vRx, organizations can outpace ransomware operators. In this adversarial game, speed and visibility win and Vicarius brings both.














