

Feature
xTags
xTags take into account internal use and external intel to enumerate and quantity factors that contribute to risk. Rich contextual data indicates risk faster and more accurately.

80
%
Reduction in time spent on manual patching
22
days
Average Mean Time To Remediate (MTTR)
$20K+
%
In savings by consolidating tools

































































































benefits
Data-backed threat prioritization
Exploitation Likelihood
Computational engine indicate likelihood of exploitation from low medium and high
Context Counts
Contextual scoring identifies prioritization parameters, access authority, activity status, and more to determine the risk level of every application and asset in your organization.
Actionable Results
More than just a quantifiable calculation, x_tags indicate which assets need your attention most.

Hear From Our Customers






All in one platform
We chose Vicarius vRx for efficient third-party software patching, as Microsoft's solutions fall short. Though challenging for servers, it's effective for end-user devices. We value its patching ability but desire a cloud testing environment. We've considered alternatives, but vRx excels in support.

Michael Sutherland
IT Security Manager at Jamaica Broilers Group






From urgency to strategy
“Vicarius allowed us to step away from reactive patching and finally manage vulnerabilities with strategy instead of urgency.”

Anonymous IT Division Manager
IT Division Manager






EL AL secures global Patch Compliance
“Within two weeks we decided on Vicarius. Patch scheduling is now a one-day task instead of a full-time job.”

Tal Shachar
Deputy Director, Infrastructure, EL AL Airlines






Complete Vulnerability Remediation Platform
"What stood out was that it wasn’t just a scanner or a patch manager. It was an entire remediation platform. You discover vulnerabilities, prioritize based on real risk, and remediate automatically."

Eric Dowsland
Chief Customer Officer






Valuable resources saved
"Before vRx, we would spend countless hours manually finding and verifying patches. We saved so much time (and headache!)."

Anonymous IT Operations Lead
IT Operations Lead






Third-party software patching is the most valuable feature.
"We have automated third-party patching on specific software, improving efficiency by 80%. vRx has reduced our patching time, which has improved our operations. It is more robust than other solutions because it offers better third-party remediation."

Billy Turner
VP, Managed Technology & Services






Single source of truth, capable of handling any application in our fleet
"vRx gives a single pane of glass to see what patches needed to go out and what sort of vulnerabilities we have on our Windows machines. Our meantime to remediate vulnerabilities has gone down by about 60% to 70%."

Peter Fallowfield
IT Manager






60% faster remediation, many hours saved
"Typically, with our previous solution of ManageEngine, it took about three hours to patch Windows Server, and now, that is less than an hour. It means less downtime for the business each month when we do patches."

Anonymous Security Analyst
Security Analyst






Great patching capabilities, helpful dashboard, and excellent support
"vRx has saved us an incredible amount of time. We can just rely on the automated system and the schedules we've set. It's a huge time saver. It's saved us hundreds of hours."

Michael Cortez
Sr. Director of IT






My favorite feature is Patchless Protection
"With Vicarius' vRx, I've never seen a patch that failed or had to be rolled back. We're saving quite a bit of time. Our clients using vRx haven't had any issues, and they've easily established patching for all their endpoints."

Jeremy Herman
Security Engineer






Unified vulnerability discovery, prioritization, and remediation
"Vicarius streamlines vulnerability management between IT & Security by directly linking identified vulnerabilities to required patches, enhancing efficiency. The automation process has saved at least 30 percent of our manual tasks."

Wayne Ajimine
Information Security Professional






Patchless Protection is an incredible technology!
"vRx reduces the time customers spend on patching by reducing the overhead on the administrators, allowing them to do additional work. It saves time they would spend addressing the patching process, follow-ups, etc."

Antwune Gray
VP IT Security and Services






Merge Security & IT to Remediate Threats
“Vicarius’s vRx enabled Adama to centralize and consolidate work between IT and security teams, leading to a more efficient patching workflow."

Oshri Cohen
CISO


Explore features
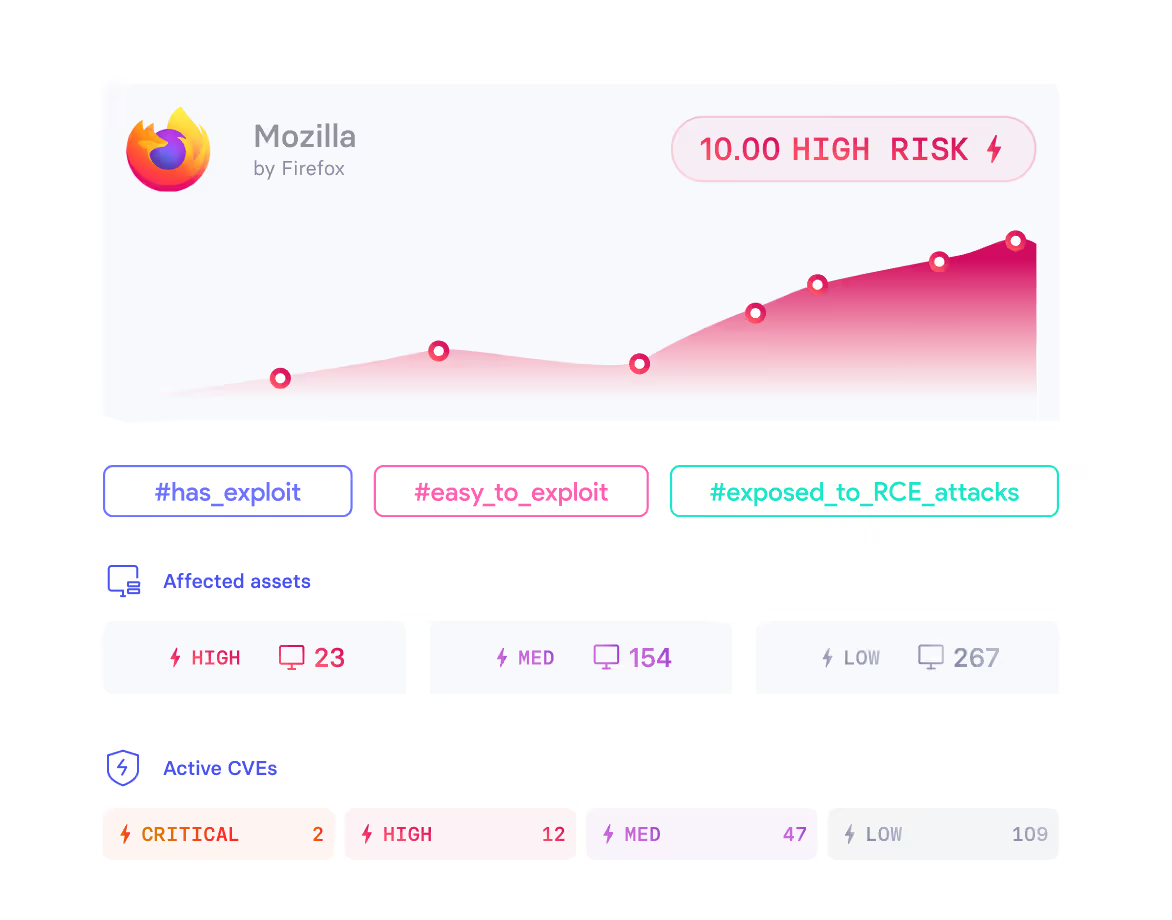
vRx Analysis
vRx analyzes the historical context of every asset and the risk factors associated with it. It monitors how these factors evolve over time to provide a full historical progression of risk.

Asset Management
Get more control than ever before with vRx asset management. Choose how to group based on asset type, location, or custom categorization to unlock the most efficiency within your teams.
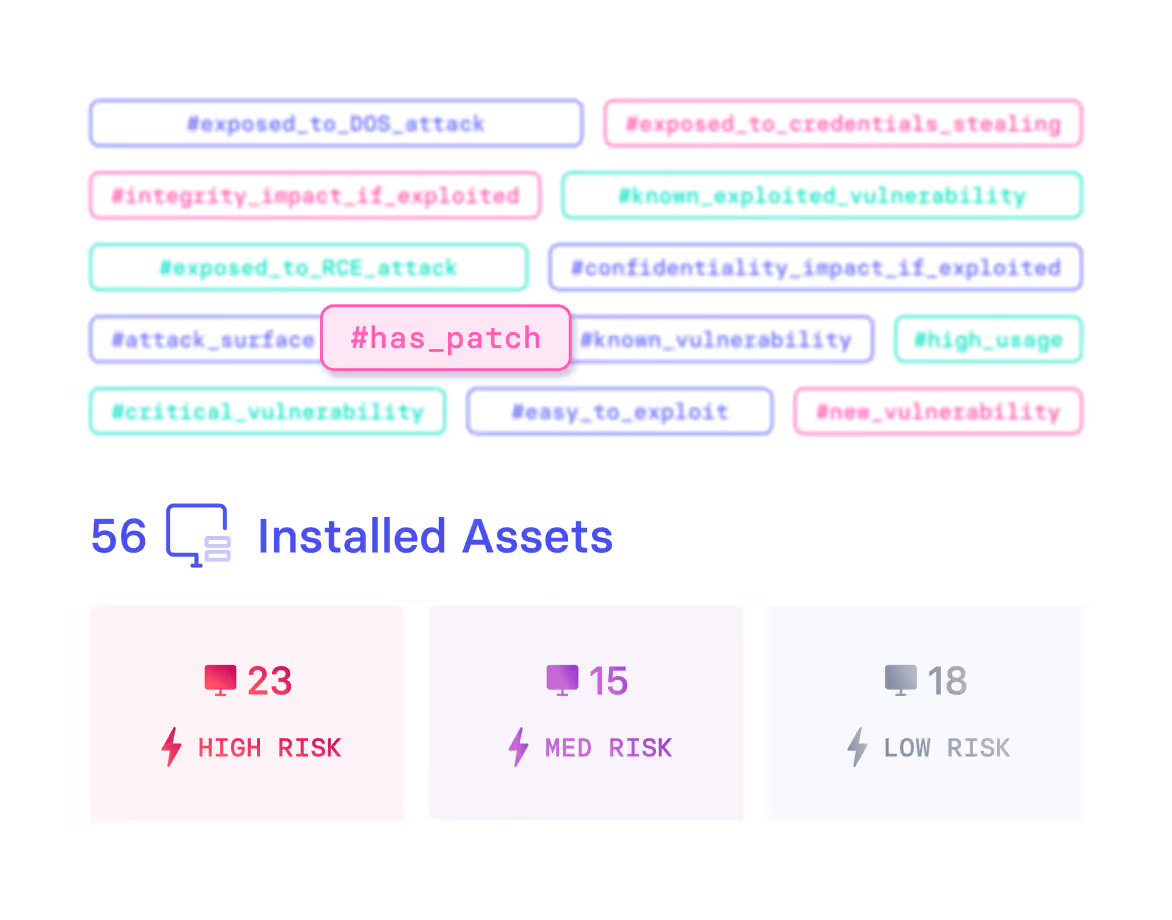
xTags
xTags take into account internal use and external intel to enumerate and quantity factors that contribute to risk. Rich contextual data indicates risk faster and more accurately.

Scripting
The vRx Scripting Engine is designed to supercharge security operations. Choose from a plethora of publicly available scripts or create your own. Supports Mac, Windows, and Linux.
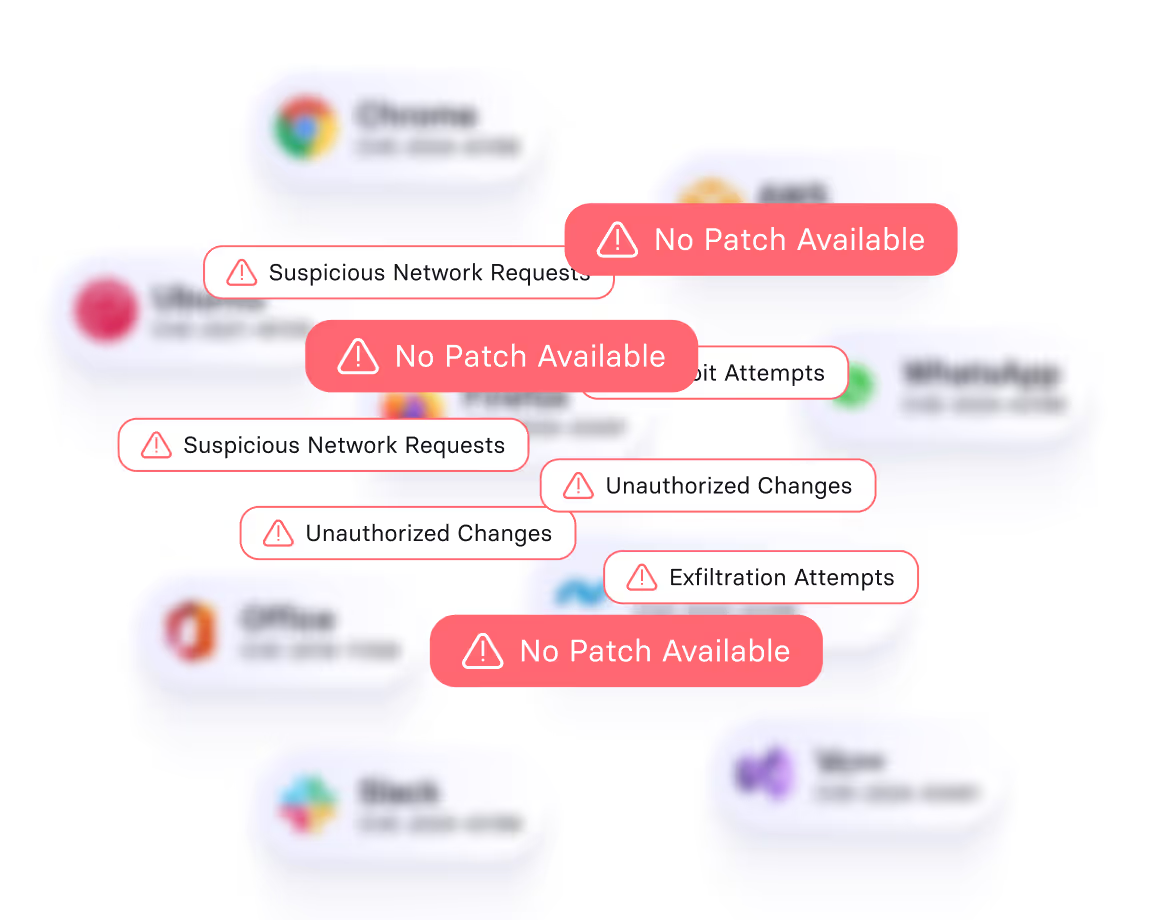
Patchless Protection
A proprietary in-house technology that protects vulnerable apps without a patch. Secures the memory space and executables from attacks, bridging the gap from disclosure to patch release.
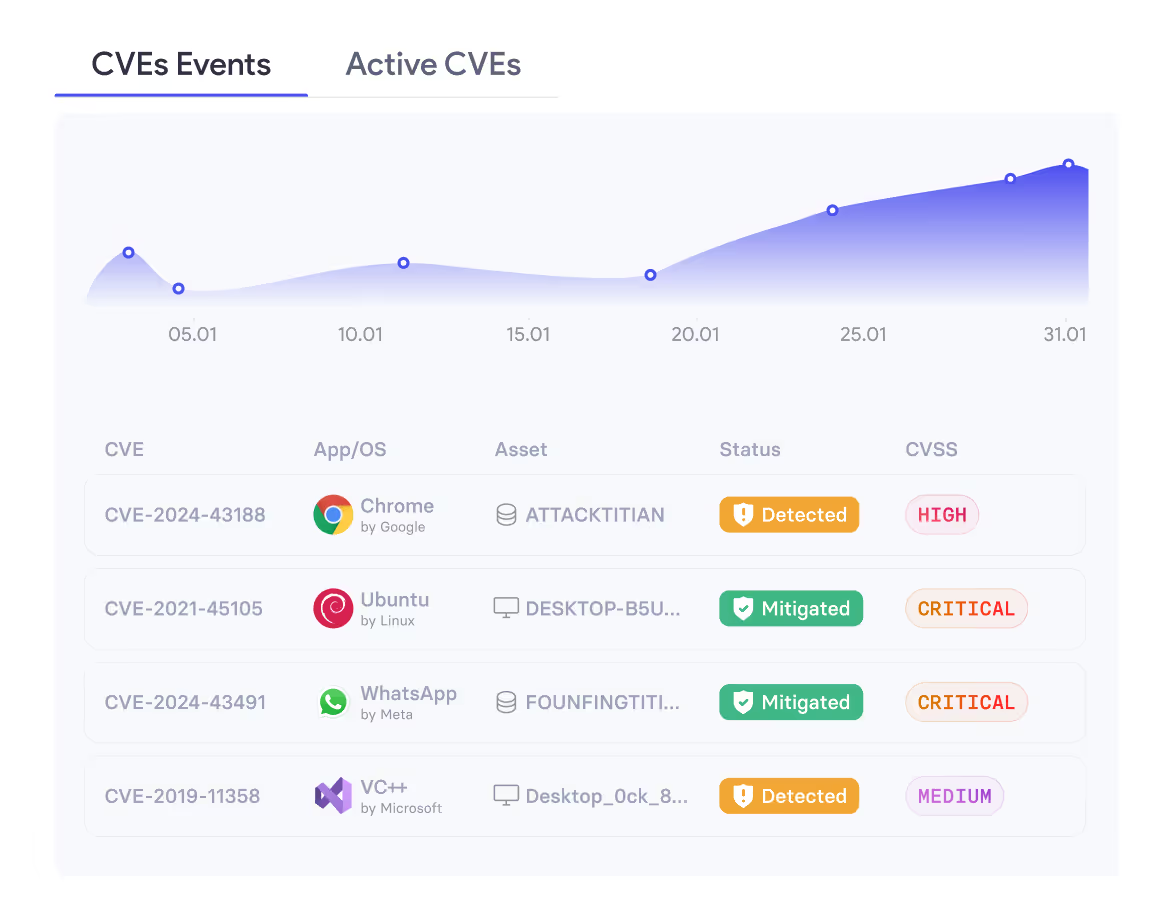
Vulnerability Discovery
Real-time asset inventory combined with all the latest disclosure data and research available brings you unparalleled visibility of every vulnerability in your network.

App & OS Coverage
vRx provides maximum coverage across thousands of apps and supports every major operating system, equipping your security and IT with security breadth and depth.
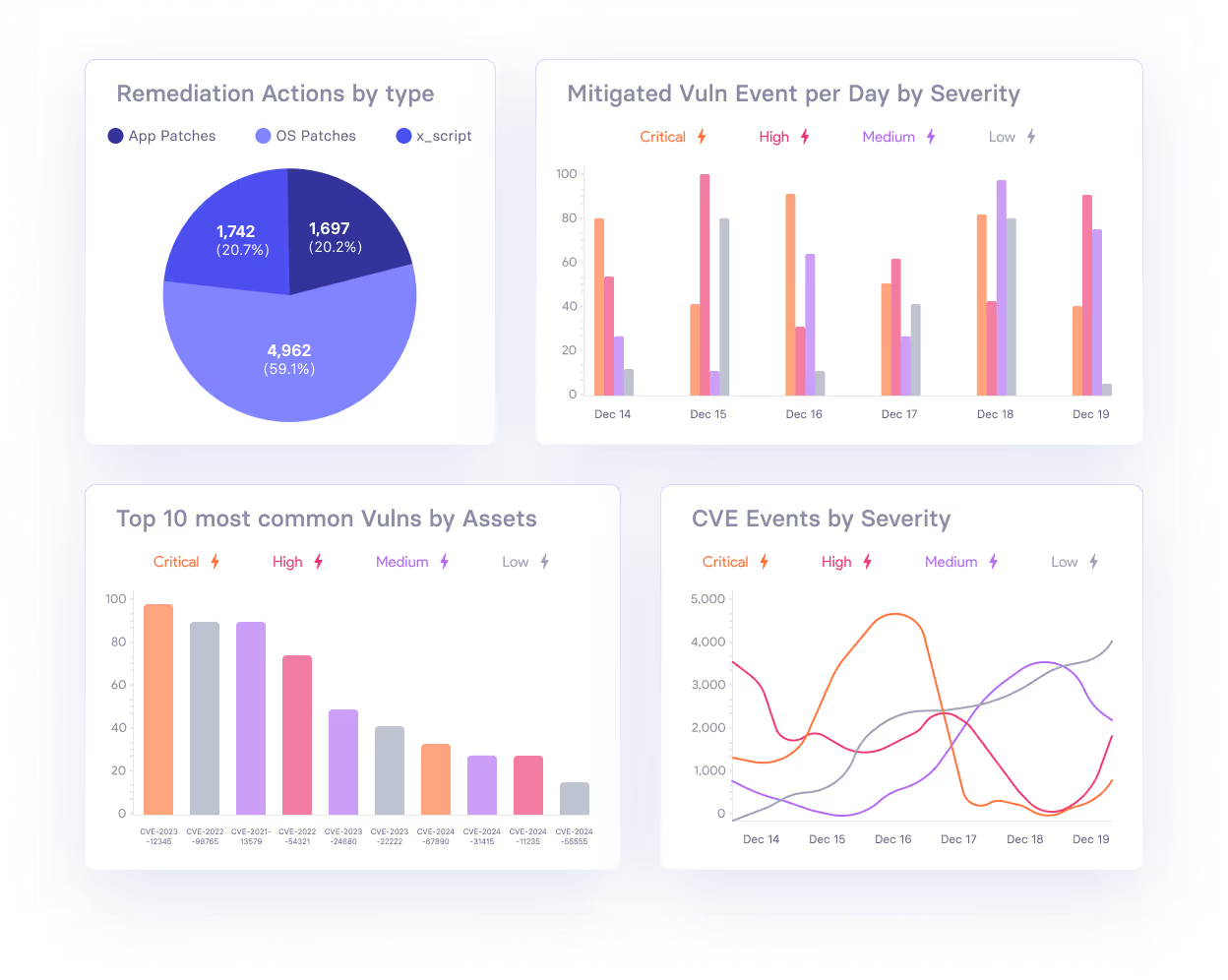
vAnalyzer
vAnalyzer is a business intelligence (BI) tool that transforms raw vulnerability data into meaningful insights. Natively integrating with vRx, vAnalyzer allows security teams to track remediation progress and generate reports in a few clicks.

User Management & Teams
Invite every member from your team, whether operator, admin, or executive, and get them all on the same page. Cross-department collaboration is right at your fingertips with customizable roles.

Automation
Make your workflow frictionless with vRx’s automation tools. From patch deployment, app installation, reporting and more, the potential time savings are exponential.
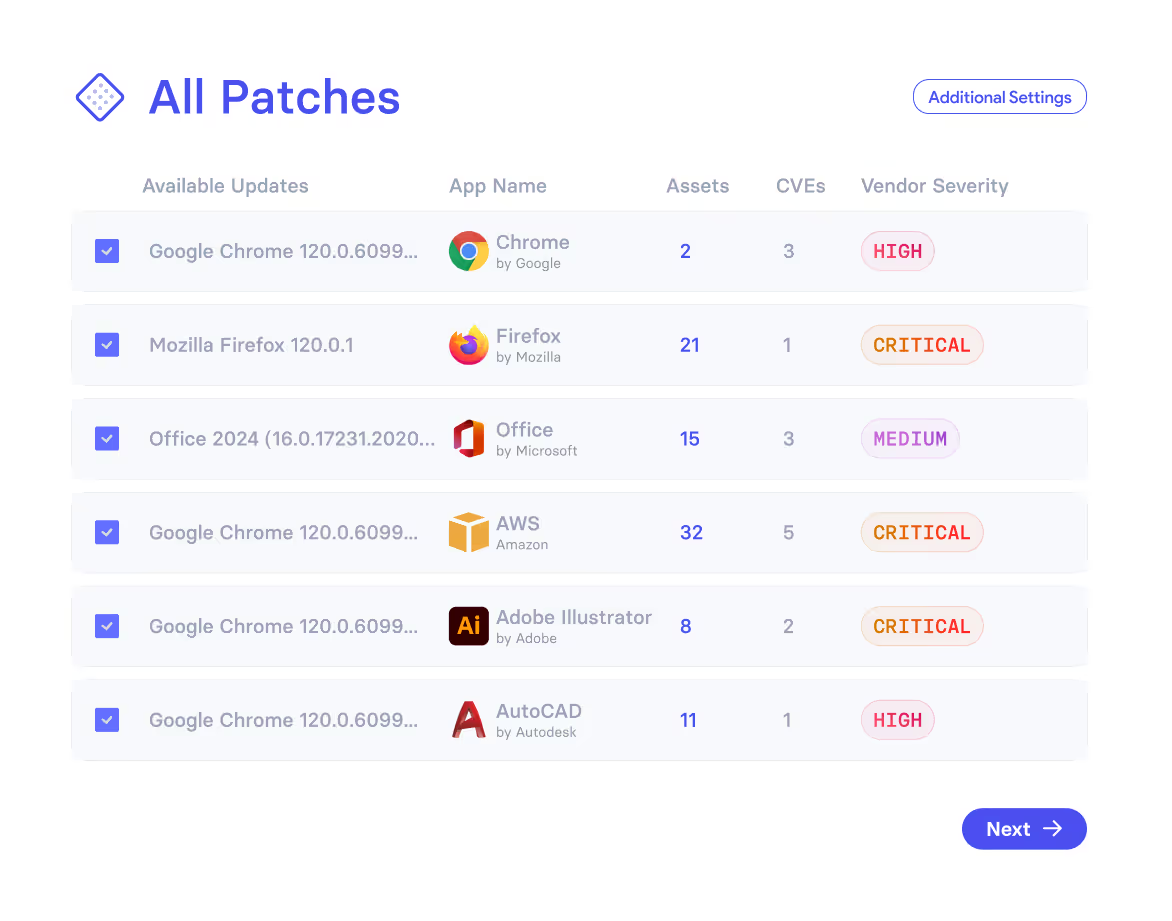
Patch Management
For all known vulnerabilities, vRx provides native patching with frictionless deployment. Never rely on additional integrations again.
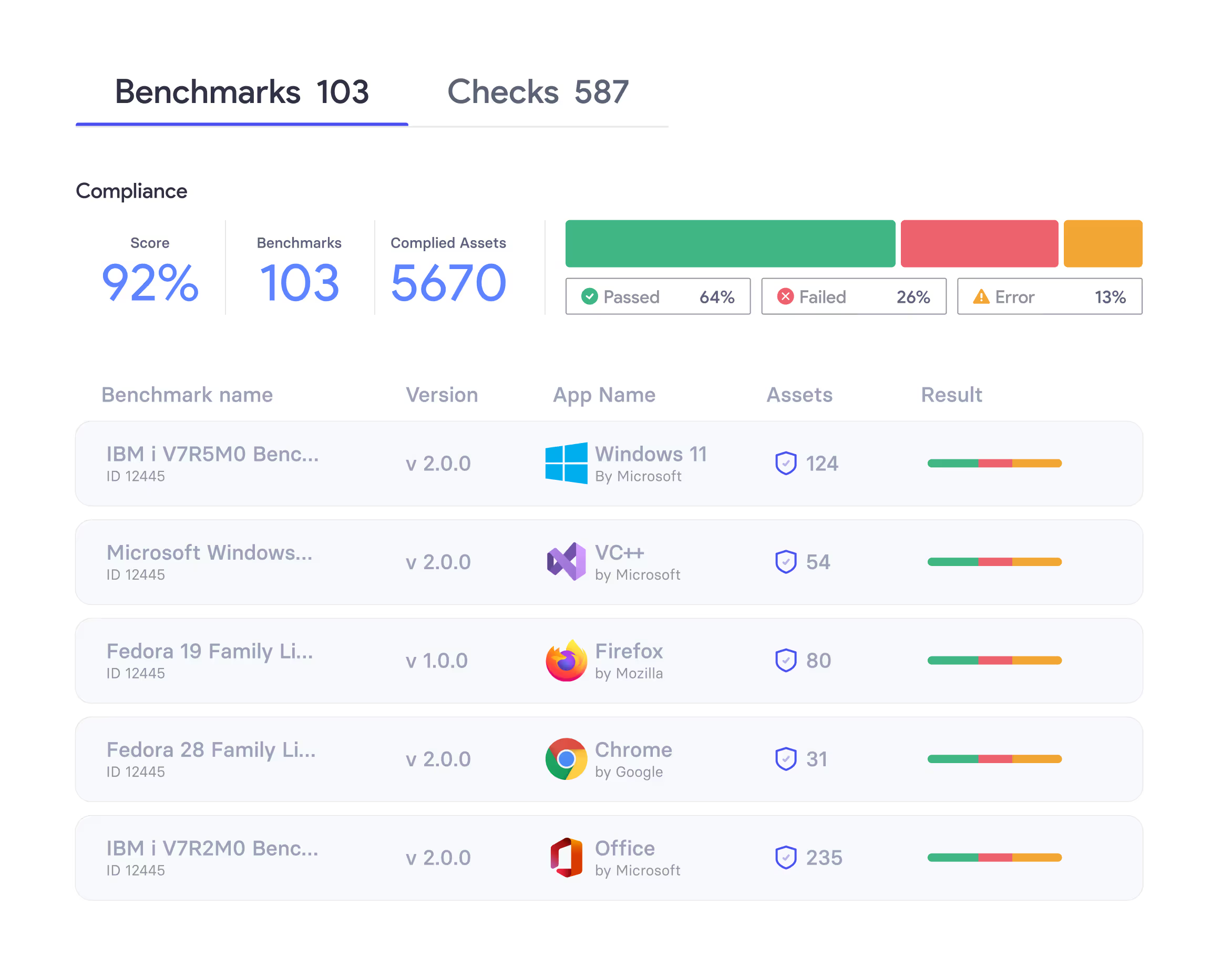
Compliance
The vRx Compliance Engine gives IT and security teams instant visibility into misconfigurations across systems and apps. With built-in, lightweight scanning and preemptive exposure management, it helps reduce risk, simplify compliance, and strengthen security hygiene without added tools or complexity.















