
Articles
Vulns & more
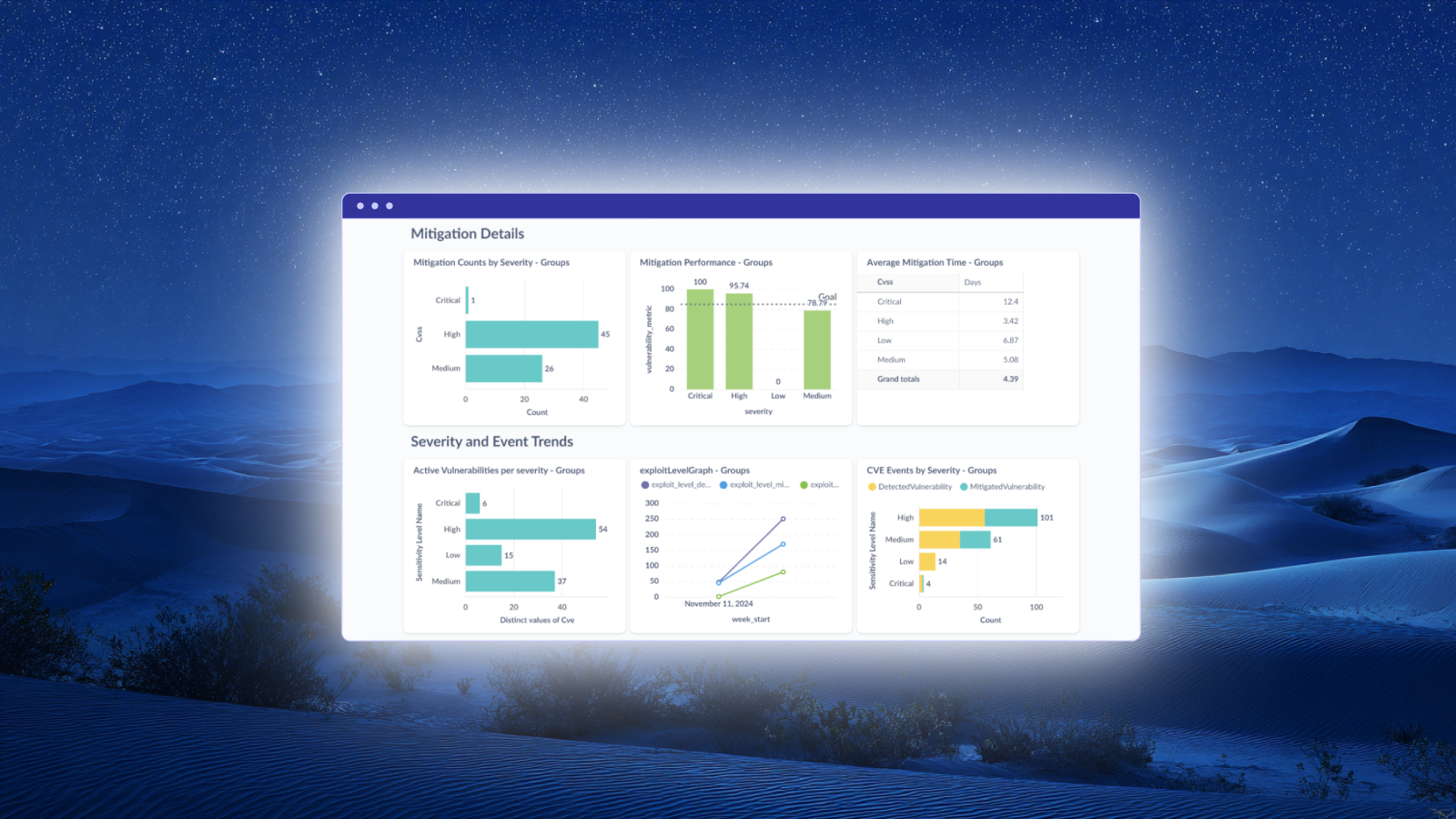
The most popular reports in Vicarius vAnalyzer
Explore the most popular vAnalyzer reports and see how Vicarius turns vulnerability data into actionable intelligence with real-time dashboards, metrics, and compliance-ready insights.


Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
Subscribe for more
Get more infosec news and insights.









