Executive Summary
Vicarius vRx ingests vulnerability and asset data from embeded scanners, agents, and threat-intelligence feeds, and other 3rd party sources, then normalizes everything into a unified model. This gives security teams a single, consistent view of their exposure across tools and enables risk-based prioritization, analytics, and automated remediation from one platform.
The Multi-Scanner Challenge
vRx can operate using its embedded vulnerability scanner, working in conjunction with deployed endpoint agents and a network scanning agent. Together, these components discover active machines and network devices across the environment and identify their associated vulnerabilities. In parallel, vRx integrates with third-party scanners, cloud security platforms, and threat intelligence feeds.
Each source produces data in different formats, with inconsistent severity scales, identifiers, and field structures. This fragmentation forces security teams to manually correlate findings, maintain separate dashboards, and reconcile overlapping or conflicting results.
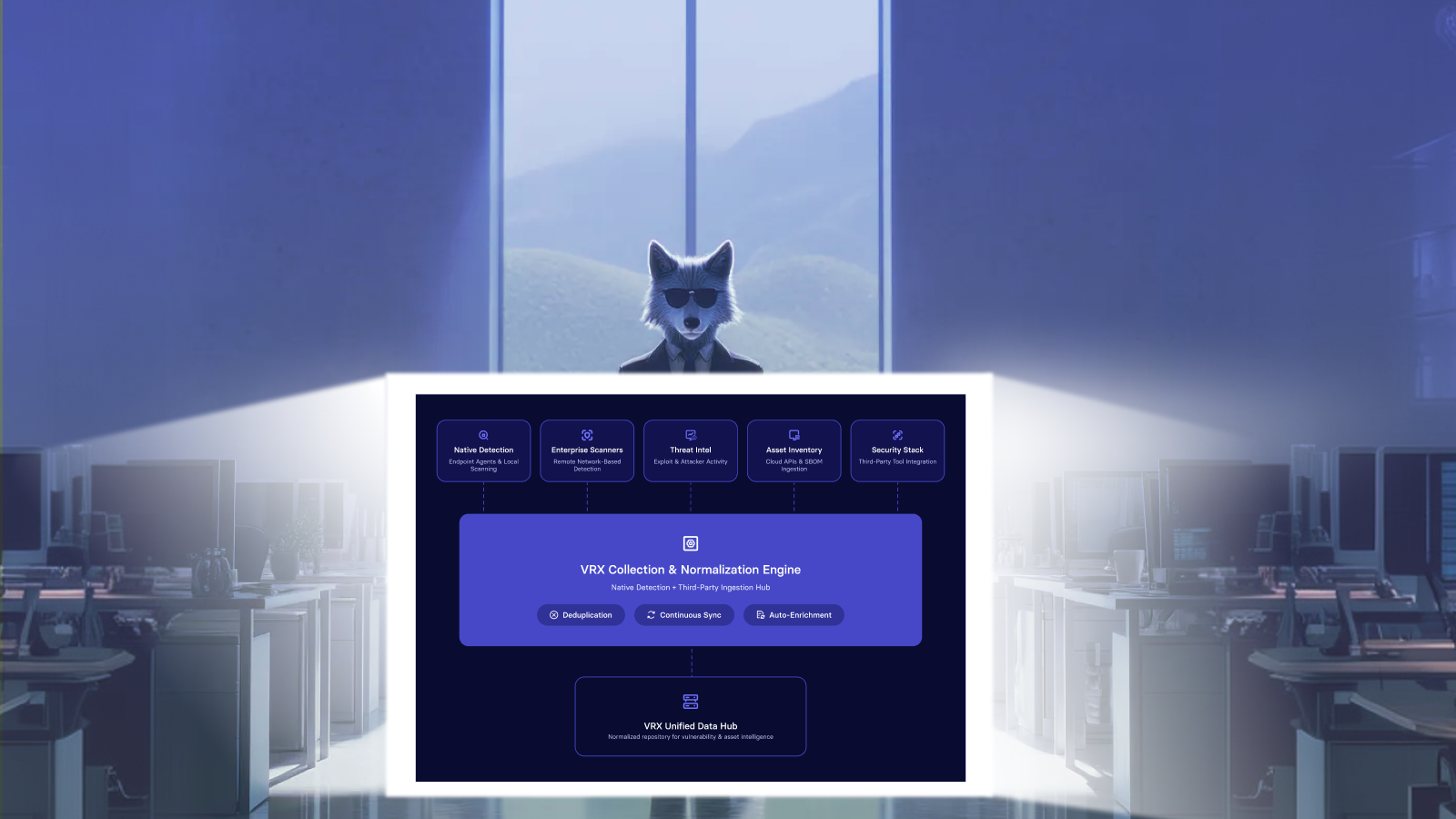
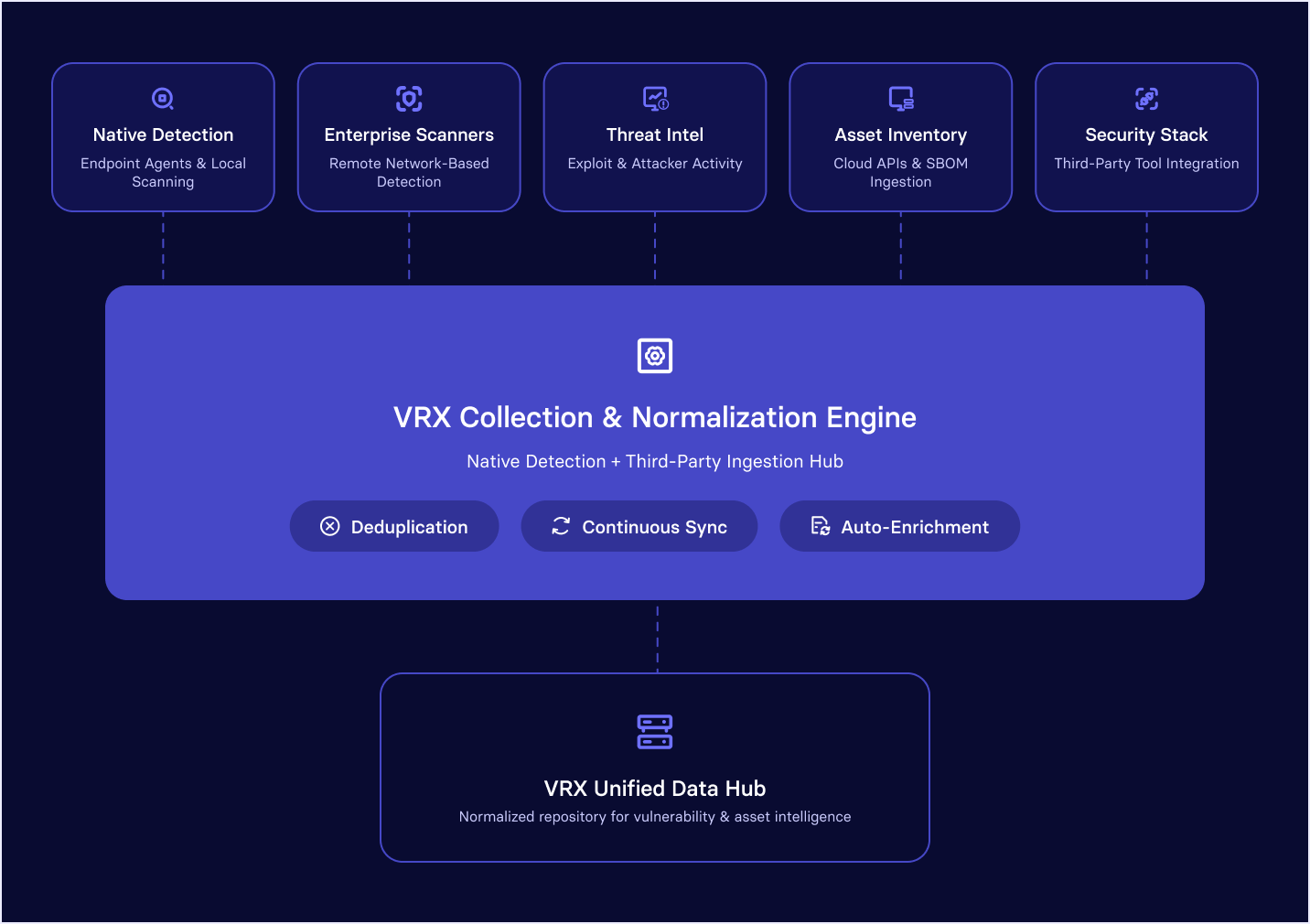
vRx Data Collection Architecture
vRx collects vulnerability and asset data through a combination of native detection capabilities and third-party integrations:
- Native Embedded Scanning - Endpoint agents and a network scanning capabilities work together to discover active machines and network devices and identify their associated vulnerabilities
- Network and Remote Scanners - Integration with enterprise scanners for additional network-based vulnerability detection
- Threat Intelligence Feeds - Threat intelligence vendors, vendor security advisories, and exploit and attacker activity data
- Asset Inventory Sources - Native agents, agentless scans, Software Bill of Materials (SBOMs), and cloud provider APIs
- Third-Party Security Tools - Ingestion from the existing security stack without requiring tool replacement
The Normalization Engine
Every scanner and feed uses different field structures, severity scoring, and identification schemes. vRx's normalization engine maps all inputs into a single, scanner-agnostic vulnerability evidence model.
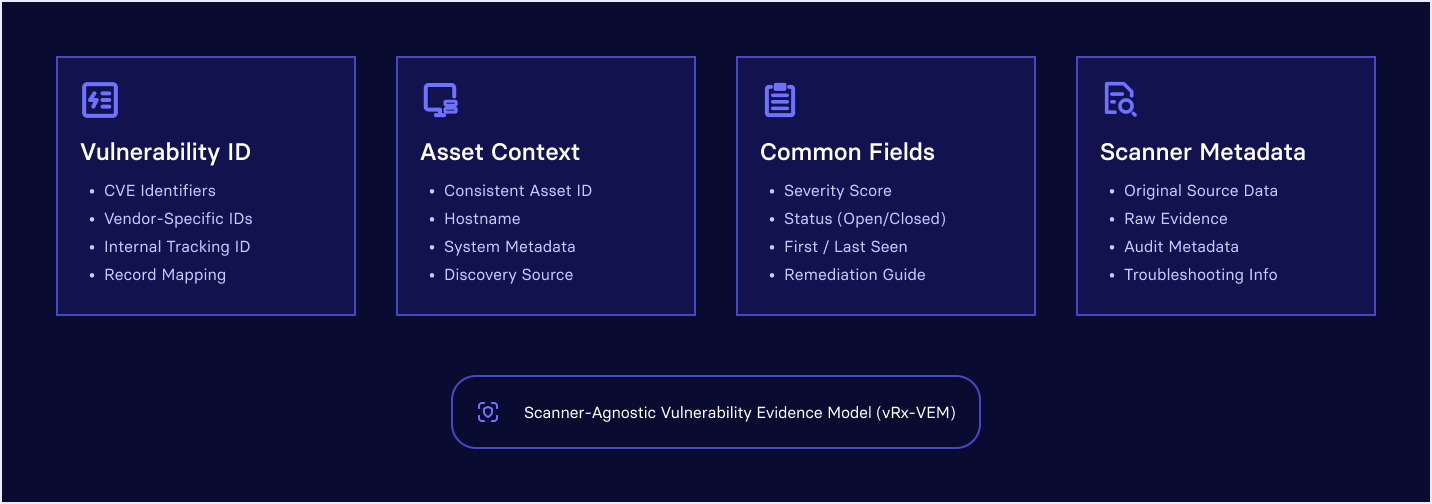
Unified Data Model
The normalized schema includes:
- Vulnerability Identification - CVE identifiers, vendor-specific IDs, and internal tracking IDs mapped to a single record
- Asset Context: Consistent asset ID, hostname, and system metadata regardless of discovery method
- Common Fields: Severity score, status, first seen/last seen timestamps, detection evidence, and remediation guidance
- Scanner Metadata: Original source-specific details preserved for audit and troubleshooting
Lifecycle Tracking
vRx tracks each finding across its complete lifecycle from initial discovery through validation, remediation, and potential recurrence. This provides a single, trusted record of each vulnerability on each asset, regardless of which scanner or feed originally detected it.
Capabilities Enabled by Normalization

Integration Workflow

- Connect Data Sources: Deploy endpoint agents and the network scanning agent, configure integrations with existing scanners, or connect cloud provider APIs
- Automatic Ingestion: vRx continuously pulls vulnerability and asset data from all configured sources
- Normalization Processing: Data is mapped to the unified schema, deduplicated, and enriched with threat intelligence
- Unified Output: Access normalized findings via UI dashboards, APIs, or automated remediation workflows
Summary
vRx's collection and normalization architecture eliminates the operational burden of managing disparate vulnerability data sources. By creating a single source of truth for vulnerability findings, security teams can focus on risk reduction rather than data reconciliation enabling faster, more accurate remediation decisions across the entire environment.